This post provides a retrospective analysis of Mirai — the infamous Internet-of-Things botnet that took down major websites via massive distributed denial-of-service using hundreds of thousands of compromised Internet-Of-Things devices.
At its peak in September 2016, Mirai temporarily crippled several high-profile services such as OVH, Dyn, and Krebs on Security via massive distributed Denial of service attacks (DDoS). OVH reported that these attacks exceeded 1Tbps—the largest on public record.
What’s remarkable about these record-breaking attacks is they were carried out via small, innocuous Internet-of-Things (IoT) devices like home routers, air-quality monitors, and personal surveillance cameras. At its peak, Mirai enslaved over 600,000 vulnerable IoT devices, according to our measurements.
Note: This blog post was edited on Dec 6th 2017 to incorporate the feedback I received via Twitter and other channels. In particular, the link the previously largest DDoS attack reported was changed and I improved the notes about Mirai targets based on the additional information received. A big thanks to everyone who took the time to help make this blog post better.
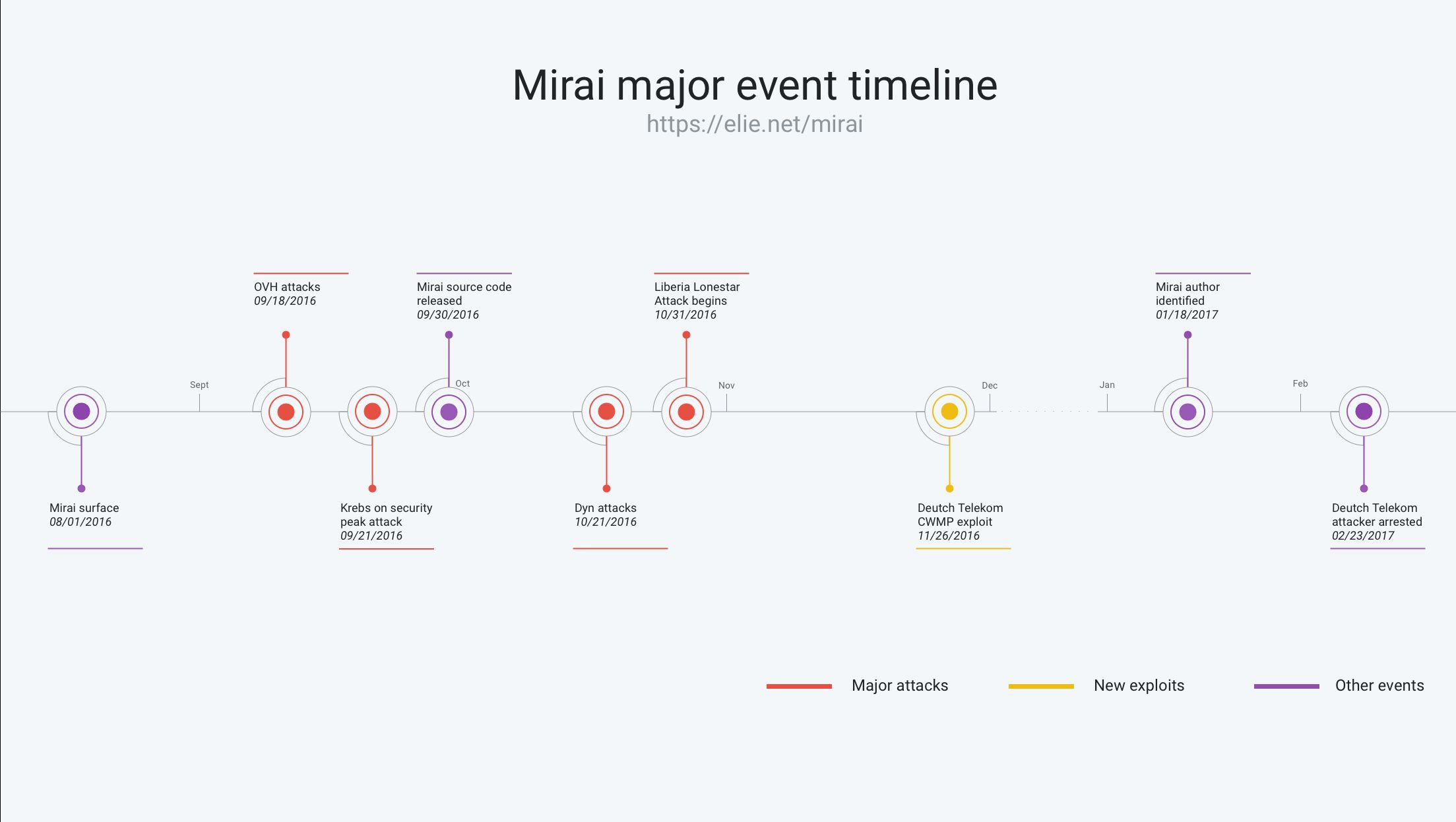
As illustrated in the timeline above (full screen) , Mirai’s story is full of twist and turns. Behind the scenes, many of these turns occurred as various hacking groups fought to control and exploit IoT devices for drastically different motives. To untangle what happened, I teamed up with collaborators at Akamai, Cloudflare, Georgia Tech, Google, the University of Illinois, the University of Michigan, and Merit Network. Together, we uncovered the Mirai backstory by combining our telemetry and expertise.
This blog post recounts Mirai’s tale from start to finish. It is based on the joint paper we published earlier this year at USENIX Security and cover the following topics:
- Mirai Genesis: Discusses Mirai’s early days and provides a brief technical overview of how Mirai works and propagates.
- Krebs on Security attack: Recounts how Mirai briefly silenced Brian Krebs website.
- OVH DDoS attack: Examines the Mirai author’s attempt to take down one of the world’s largest hosting providers.
- The rise of copycats: Covers the Mirai code release and how multiple hacking groups end-up reusing the code. This section also describes the techniques we used to track down the many variants of Mirai that arose after the release. Finally this section discusses the targets and the motive behind each major variants.
- Mirai takedown the Internet: Tells the insider story behind Dyn attacks including the fact that the major sites (e.g., Amazon) taken down were just massive collateral damage.
- Mirai’s shutdown an entire country?: Looks at the multiple attacks carried out against Lonestar, Liberia’s largest operator.
- Deutsche Telekom goes dark: Discusses how the addition of a router exploit to one of the Mirai variant brought a major German Internet provider to its knees.
- Mirai original author outed?: Details Brian Krebs’ in-depth investigation into and apparent discovery of Mirai’s author and his subsequent FBI interrogation.
- Deutsche Telekom attacker arrested: Recounts the arrest of the hacker who took down Deutsche Telekom and what we learned from his trial.
MIRAI Genesis
The first public report of Mirai late August 2016 generated little notice, and Mirai mostly remained in the shadows until mid-September. At that time, It was propelled in the spotlight when it was used to carry massive DDoS attacks against Krebs on Security the blog of a famous security journalist and OVH one of the largest web hosting provider in the world.
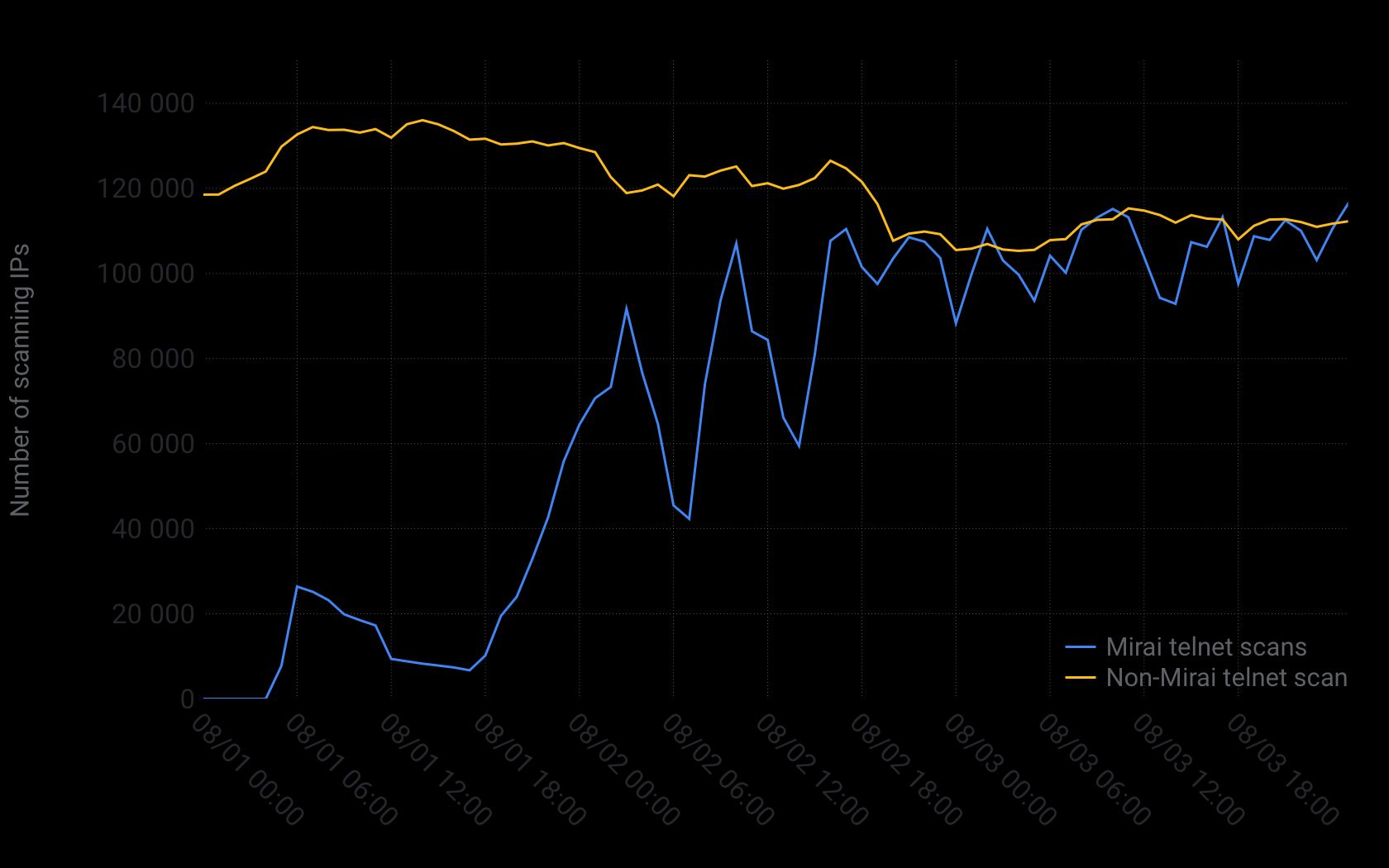
While the world did not learn about Mirai until at the end of August, our telemetry reveals that it became active August 1 when the infection started out from a single bulletproof hosting IP. From thereon, Mirai spread quickly, doubling its size every 76 minutes in those early hours.
By the end of its first day, Mirai had enslaved over 65,000 IoT devices. By its second day, Mirai already accounted for half of all Internet telnet scans observed by our collective set of honeypots, as shown in the figure above. At its peak in November 2016 MIRAI had enslaved over 600,000 IoT devices.
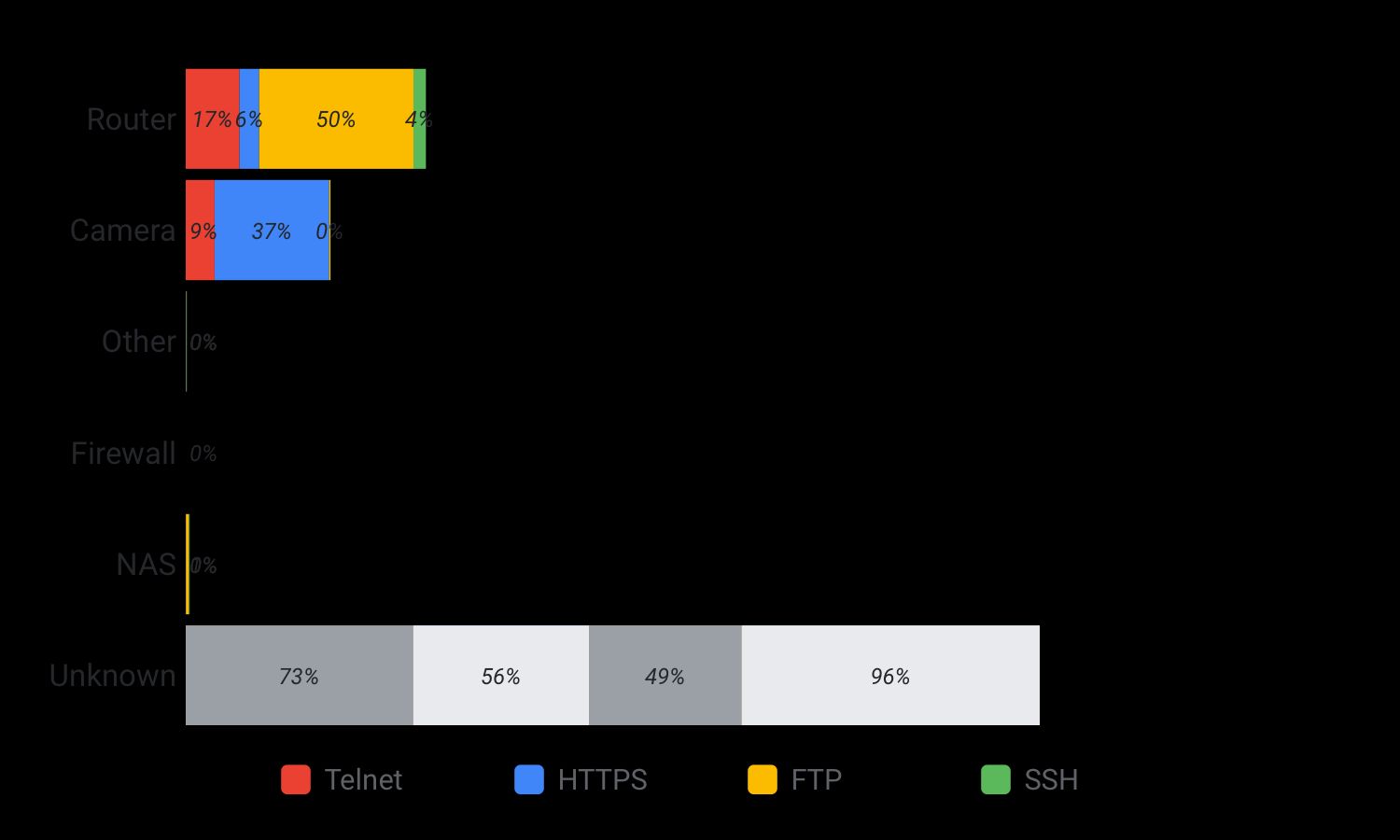
Retro-actively looking at the infected device services banners gathered thanks to Censys regular Internet wide scanning reveals that most of the devices appears to be routers and cameras as reported in the chart above. Each type of banner is represented separately as the identification process was different for each so it might be that a device is counted multiple times. Mirai was actively removing any banner identification which partially explain why we were unable to identify most of the devices.
Before delving further into Mirai’s story, let’s briefly look at how MIRAI works, specifically how it propagate and its offensive capabilities.
How Mirai works
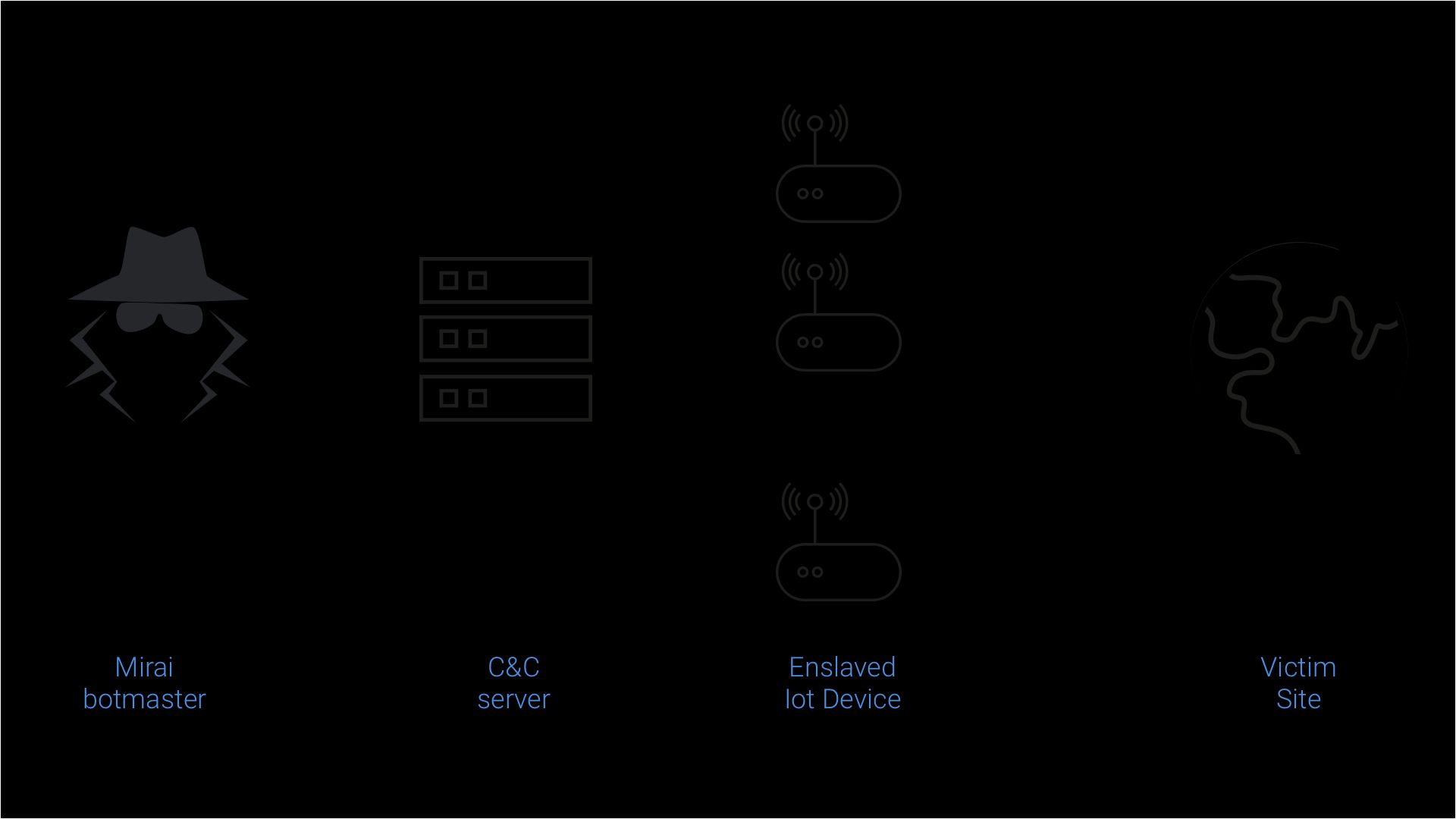
At its core, Mirai is a self-propagating worm, that is, it’s a malicious program that replicates itself by finding, attacking and infecting vulnerable IoT devices. It is also considered a botnet because the infected devices are controlled via a central set of command and control (C&C) servers. These servers tell the infected devices which sites to attack next. Overall, Mirai is made of two key components: a replication module and an attack module.
Replication module
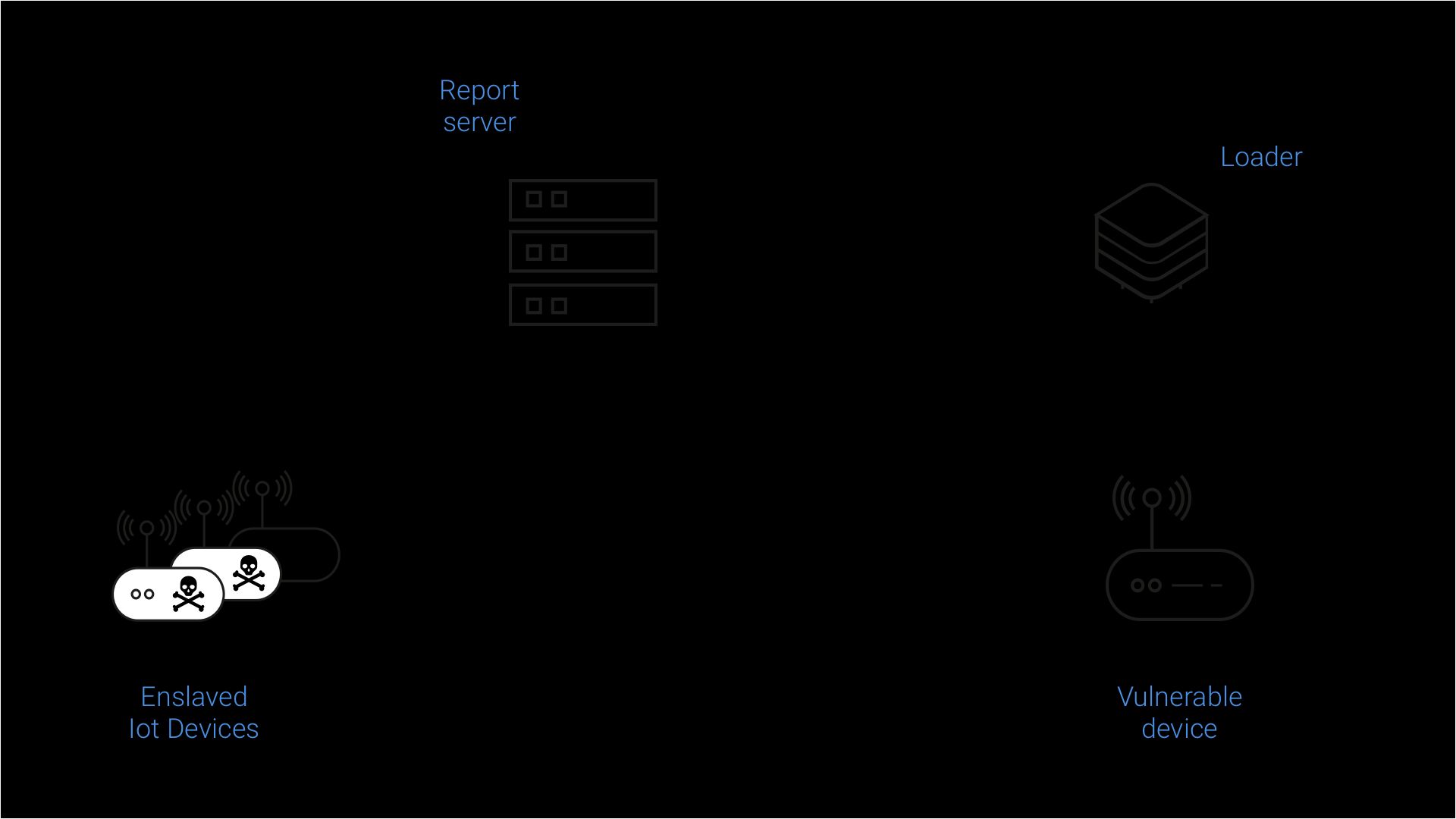
The replication module is responsible for growing the botnet size by enslaving as many vulnerable IoT devices as possible. It accomplishes this by (randomly) scanning the entire Internet for viable targets and attacking. Once it compromises a vulnerable device, the module reports it to the C&C servers so it can be infected with the latest Mirai payload, as the diagram above illustrates.
To compromise devices, the initial version of MIRAI relied exclusively on a fixed set of 64 well-known default login/password combinations commonly used by IoT devices. While this attack was very low tech, it proved extremely effective and led to the compromise of over 600,000 devices.
MIRAI was able to infect over 600,000 IoT devices by simply exploiting a set of 64 well-known default IoT login/password combinations.
Attack module
The attack module is responsible for carrying out DDoS attacks against the targets specified by the C&C servers. This module implements most of the code DDoS techniques such as HTTP flooding, UDP flooding, and all TCP flooding options. This wide range of methods allowed Mirai to perform volumetric attacks, application-layer attacks, and TCP state-exhaustion attacks. For more information on DDoS techniques, read this intro post by Arbor Network
Krebs attack
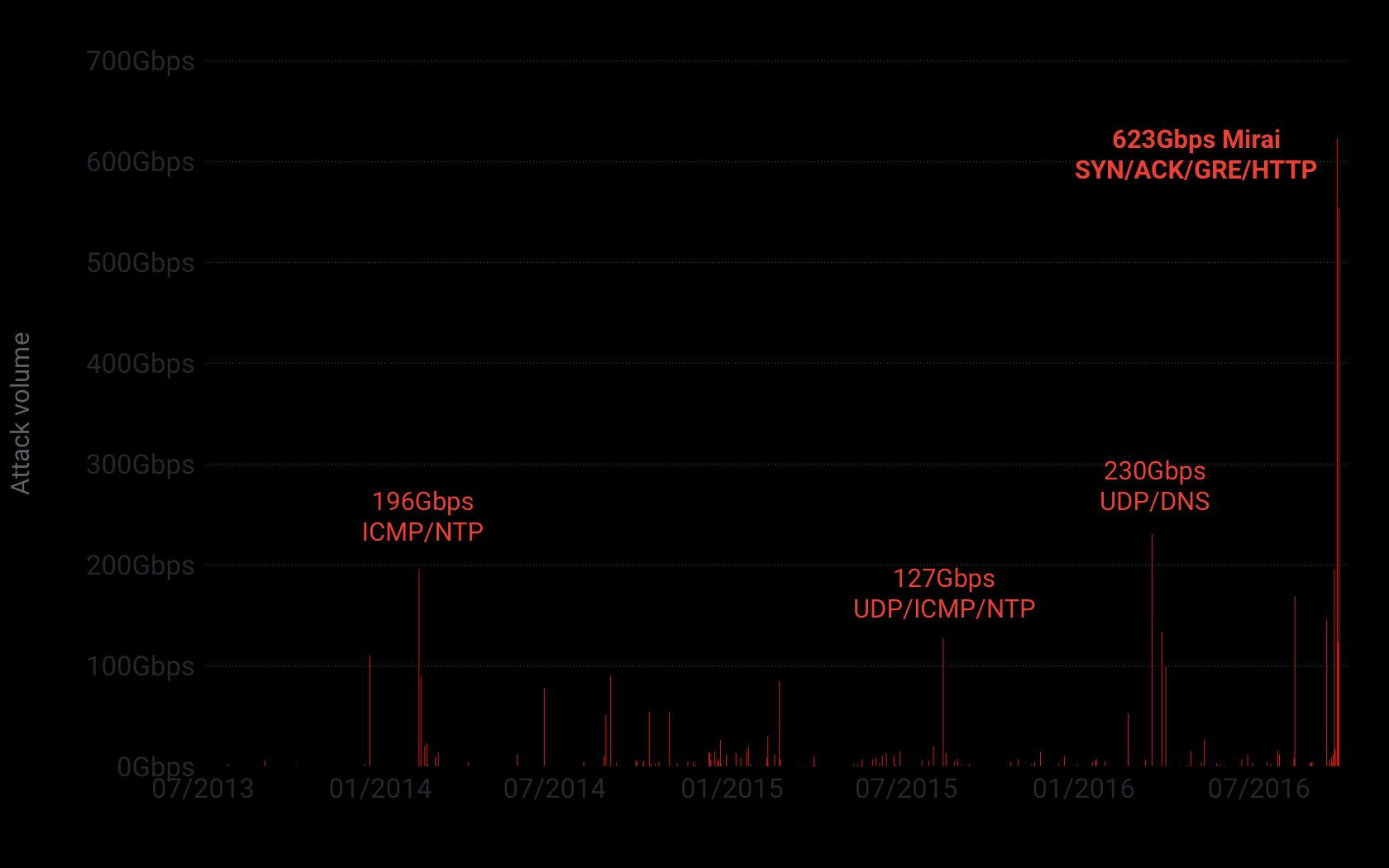
Krebs on Security is Brian Krebs’ blog. Krebs is a widely known independent journalist who specializes in cyber-crime. Given Brian’s line of work, his blog has been targeted, unsurprisingly, by many DDoS attacks launched by the cyber-criminals he exposes. According to his telemetry (thanks for sharing, Brian!), his blog suffered 269 DDOS attacks between July 2012 and September 2016. As seen in the chart above, the Mirai assault was by far the largest, topping out at 623 Gbps.
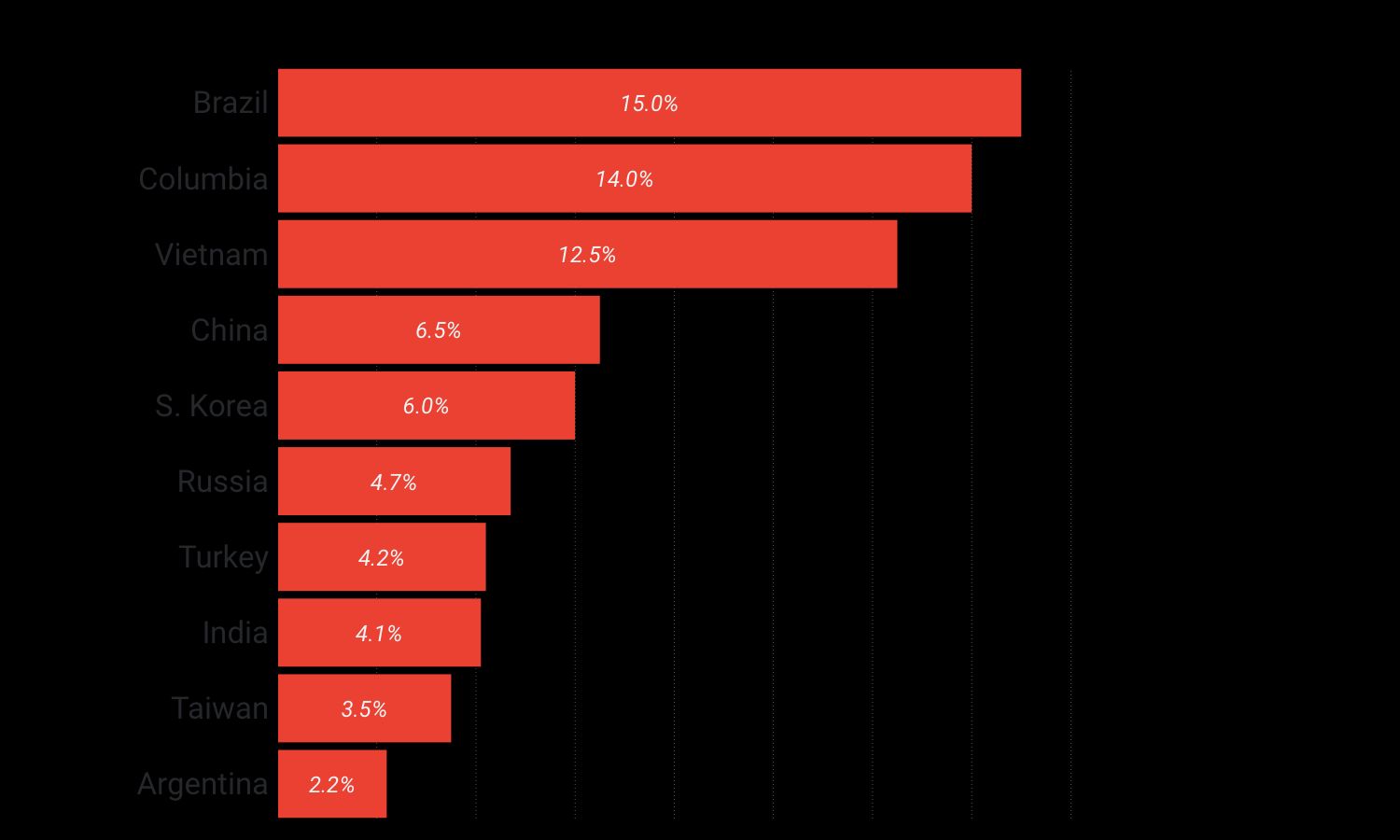
Looking at the geolocation of the IPs that targeted Brian’s site reveals that a disproportionate number of the devices involved in the attack are coming from South American and South-east Asia. As reported in the chart above Brazil, Vietnam and Columbia appears to be the main sources of compromised devices.
One dire consequence of this massive attack against Krebs was that Akamai, the CDN service that provided Brian’s DDoS protection, had to withdraw its support. This forced Brian to move his site to Project Shield. As he discussed in depth in a blog post, this incident highlights how DDOS attacks have become a common and cheap way to censor people.
OVH attack
Brian was not Mirai’s first high-profile victim. A few days before he was struck, Mirai attacked, OVH one of the largest European hosting providers. According to their official numbers, OVH hosts roughly 18 million applications for over one million clients, Wikileaks being one of their most famous and controversial ones.
We know little about that attack as OVH did not participate in our joint study. As a result, the best information about it comes from a blog post OVH released after the event. From this post, it seems that the attack lasted about a week and involved large, intermittent bursts of DDoS traffic that targeted one undisclosed OVH customer.
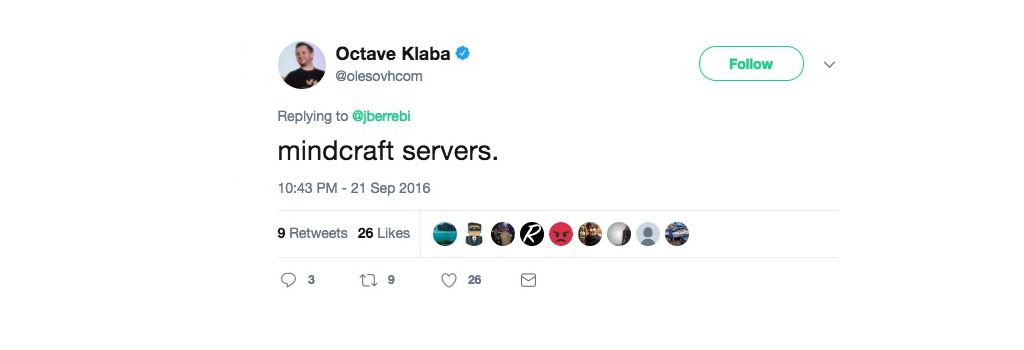
Octave Klaba OVH’s founder did report on Twitter that the attacks were targeting Minecraft servers. As we will see through this post Mirai has been extensively used in gamer wars and is likely the reason why it was created in the first place.
According to OVH telemetry, the attack peaked at 1TBs and was carried out using 145,000 IoT devices. While the number of IoT devices is consistent with what we observed, the volume of the attack reported is significantly higher than what we observed with other attacks. For example, as mentioned earlier, Brian’s one topped out at 623 Gbps.
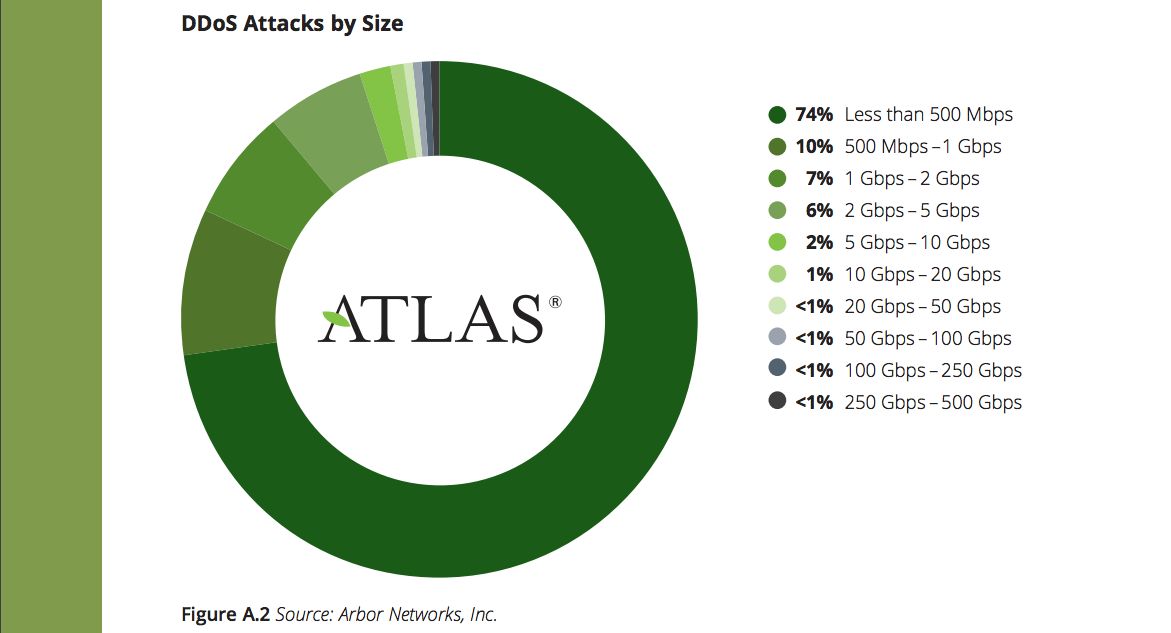
Regardless of the exact size, the Mirai attacks are clearly the largest ever recorded. They dwarf the previous “record holder,” which topped out at ~400Gpbs and even one-upped the largest ones observed by Arbor Network, which maxed out at ~800Gbps according to Arbor’s annual report.
The scale of Mirai attacks should be treated by the community as as wake-up call: vulnerable IoT devices are a major and pressing threat to Internet stability.
The rise of copycats: September 30
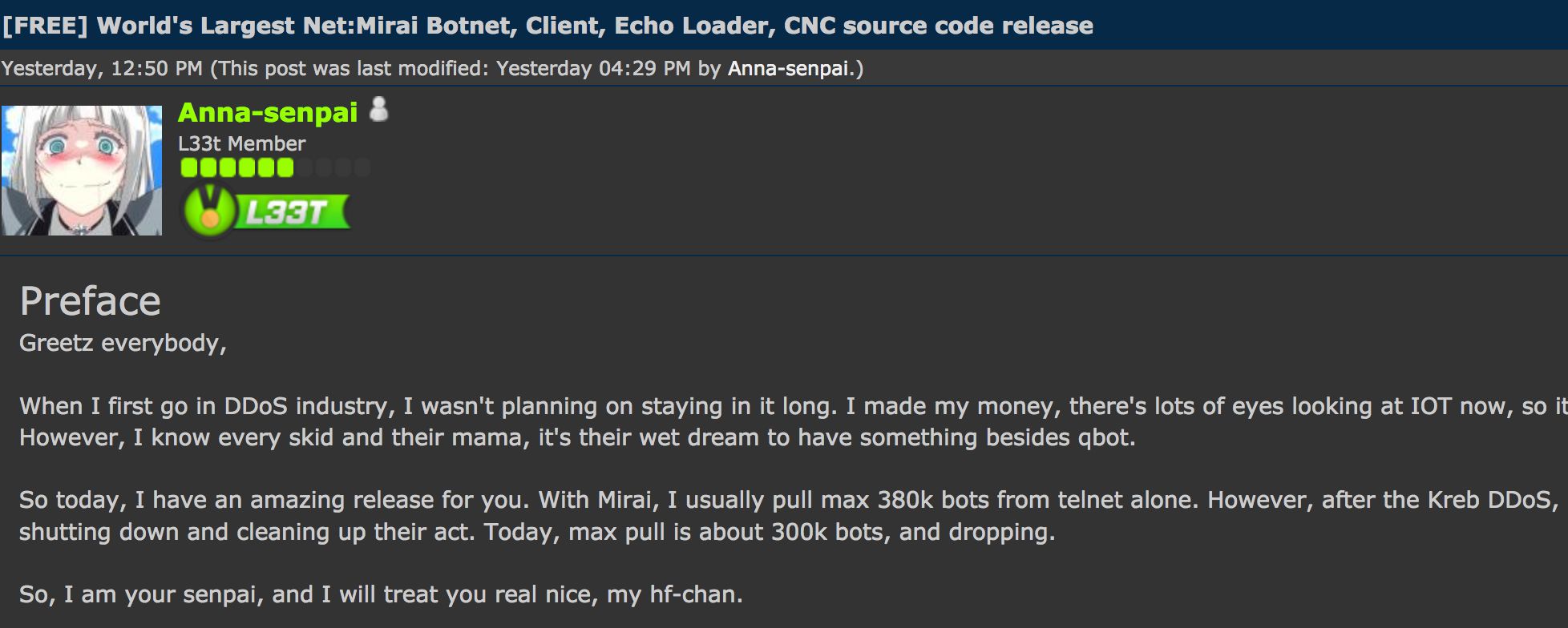
In an unexpected development, on September 30, 2017, Anna-senpai, Mirai’s alleged author, released the Mirai source code via an infamous hacking forum. He also wrote a forum post, shown in the screenshot above, announcing his retirement.
This code release sparked a proliferation of copycat hackers who started to run their own Mirai botnets. From that point forward, the Mirai attacks were not tied to a single actor or infrastructure but to multiple groups, which made attributing the attacks and discerning the motive behind them significantly harder.
Clustering Mirai infrastructure
To keep up with the Mirai variants proliferation and track the various hacking groups behind them, we turned to infrastructure clustering. Reverse engineering all the Mirai versions we can find allowed us to extract the IP addresses and domains used as C&C by the various hacking groups than ran their own Mirai variant. In total, we recovered two IP addresses and 66 distinct domains.
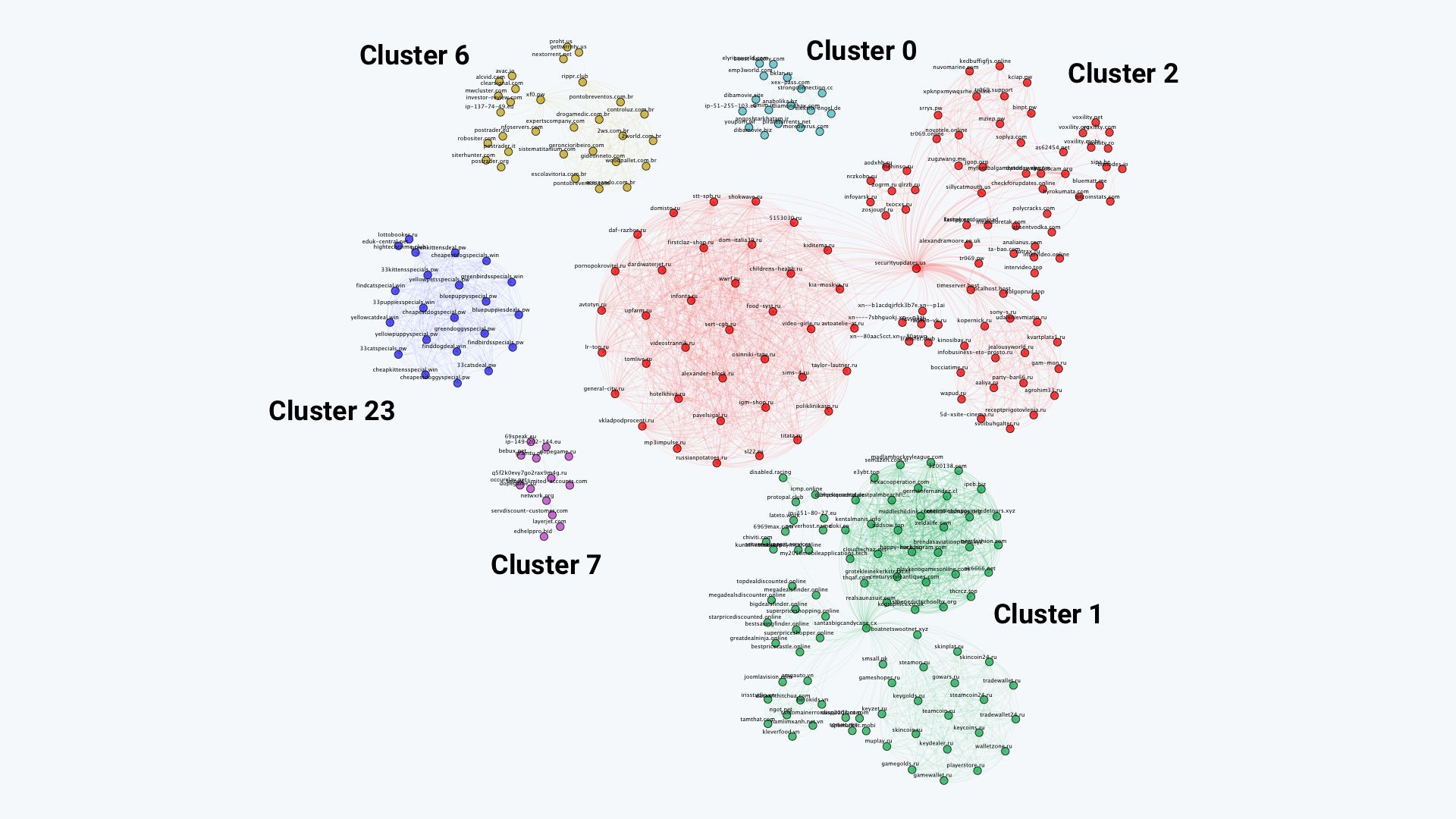
Applying DNS expansion on the extracted domains and clustering them led us to identify 33 independent C&C clusters that had no shared infrastructure. The smallest of these clusters used a single IP as C&C. The largest sported 112 domains and 92 IP address. The figure above depicts the six largest clusters we found.
These top clusters used very different naming schemes for their domain names: for example, “cluster 23” favors domains related to animals such as 33kitensspecial.pw, while “cluster 1” has many domains related to e-currencies such as walletzone.ru. The existence of many distinct infrastructures with different characteristics confirms that multiple groups ran Mirai independently after the source code was leaked.
Clusters over time
Looking at how many DNS lookups were made to their respective C&C infrastructures allowed us to reconstruct the timeline of each individual cluster and estimate its relative size. This accounting is possible because each bot must regularly perform a DNS lookup to know to which IP address its C&C domains resolves.
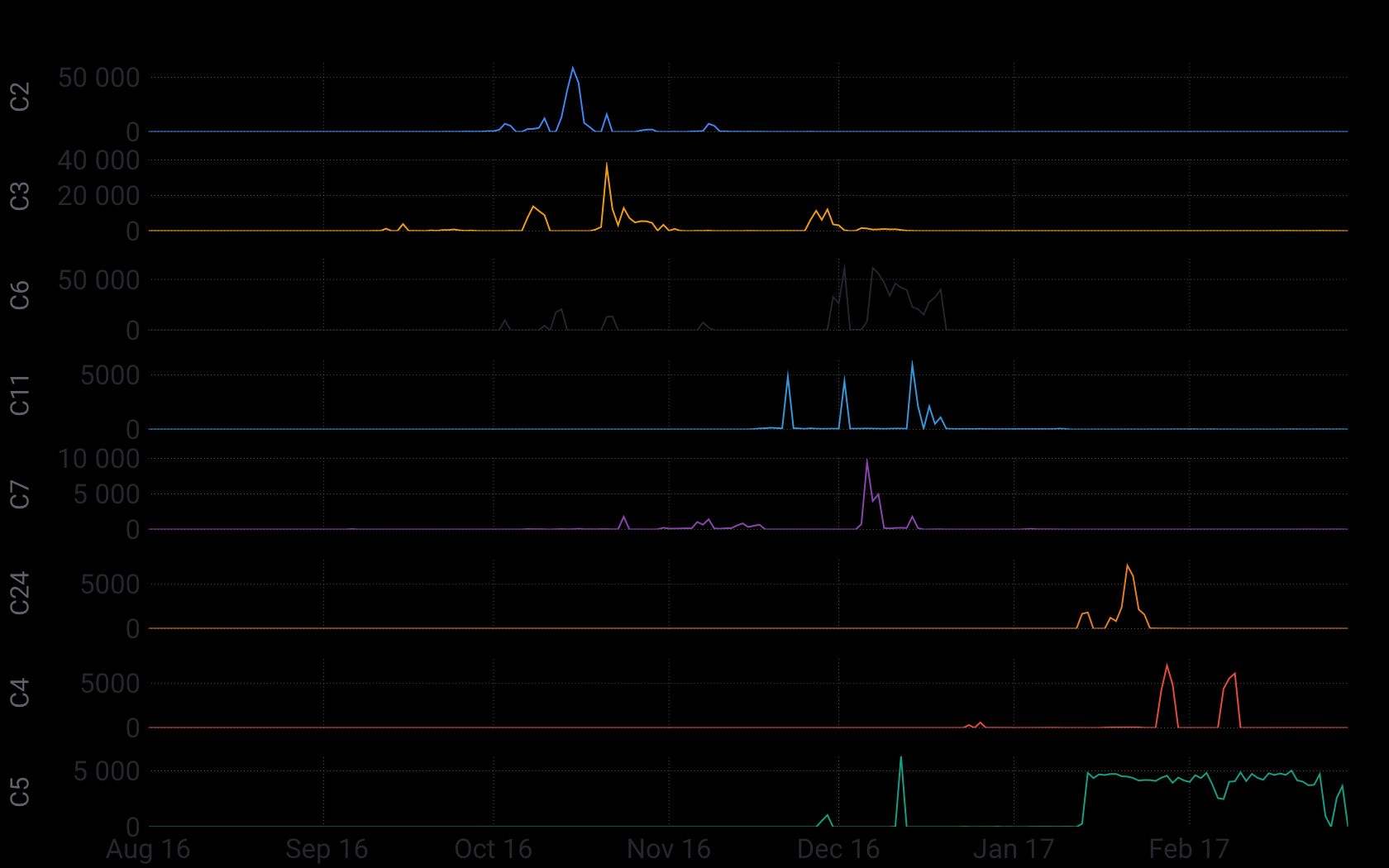
The chart above reports the number of DNS lookups over time for some of the largest clusters. It highlights the fact that many were active at the same time. Having multiple variants active simultaneously once again emphasizes that multiple actors with different motives were competing to enslave vulnerable IoT devices to carry out their DDoS attacks.
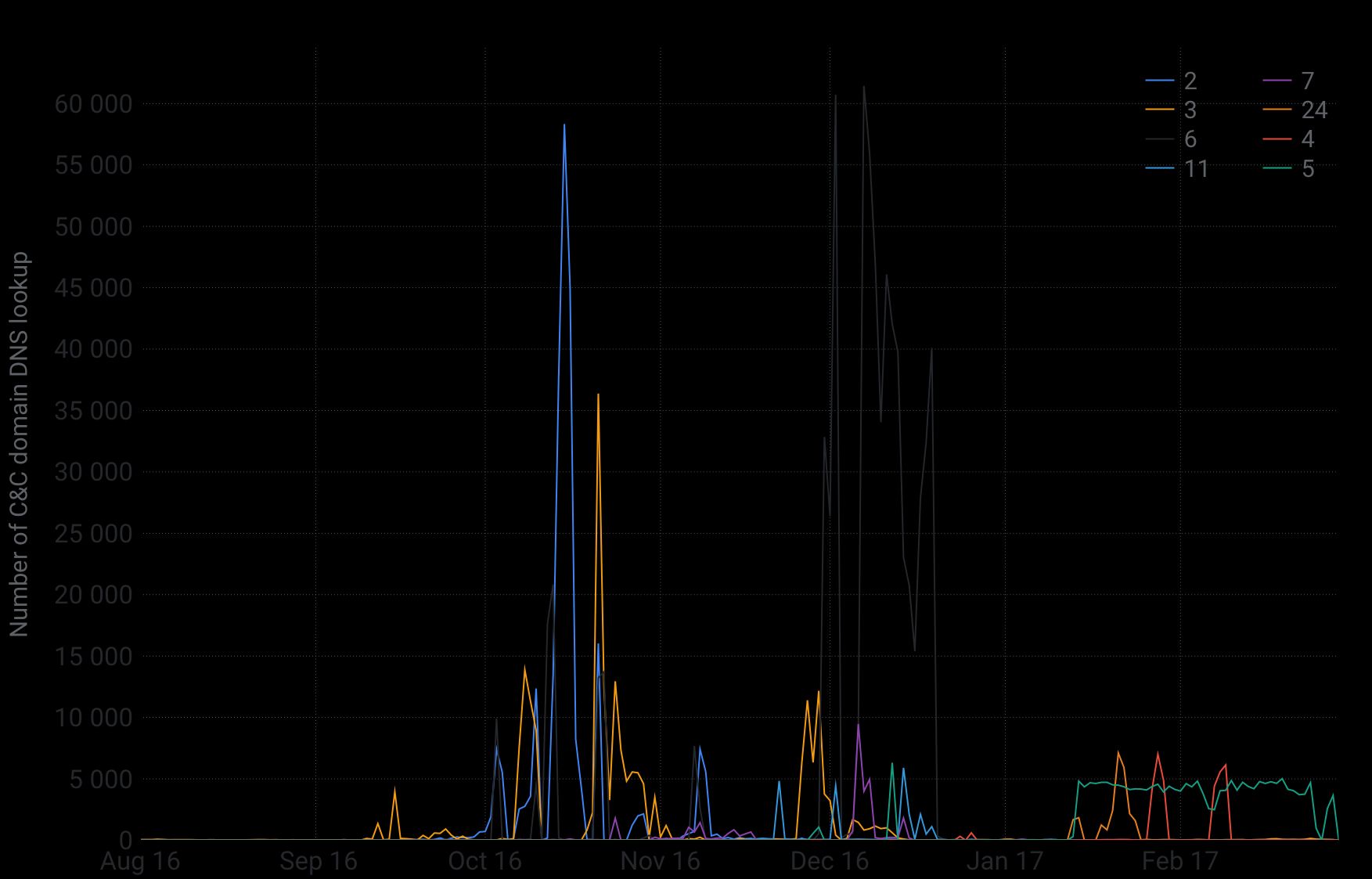
Plotting all the variants in the graph clearly shows that the ranges of IoT devices enslaved by each variant differ widely. As the graph above reveals, while there were many Mirai variants, very few succeeded at growing a botnet large enough to take down major websites.
From cluster to motive
| Cluster | Notes |
|---|---|
| 6 | Attacked Dyn and gaming related targets |
| 1 | Original botnet. Attacked Krebs and OVH |
| 2 | Attacked Lonestar Cell |
Looking at which sites were targeted by the largest clusters illuminates the specific motives behind those variants. For instance, as reported in the table above, the original Mirai botnet (cluster 1) targeted OVH and Krebs, whereas Mirai’s largest instance (cluster 6) targeted DYN and other gaming-related sites. Mirai’s third largest variant (cluster 2), in contrast, went after African telecom operators, as recounted later in this post.
| Target | Attacks | Clusters | Notes |
|---|---|---|---|
| Lonestar Cell | 616 | 2 | Liberian telecom targeted by 102 reflection attacks |
| Sky Network | 318 | 15, 26, 6 | Brazilian Minecraft servers hosted in Psychz Networks data centers |
| 104.85.165.1 | 192 | 1, 2, 6, 8, 11, 15 … | Unknown router in Akamai’s network |
| feseli.com | 157 | 7 | Russian cooking blog |
| Minomortaruolo.it | 157 | 7 | Italian politician site |
| Voxility hosted C2 | 106 | 1, 2, 6, 7, 15 … | Known decoy target |
| Tuidang websites | 100 | — | HTTP attacks on two Chinese political dissidence sites |
| execrypt.com | 96 | -0- | Binary obfuscation service |
| Auktionshilfe.info | 85 | 2, 13 | Russian auction site |
| houtai.longqikeji.com | 85 | 25 | SYN attacks on a former game commerce site |
| Runescape | 73 | — | World 26th of a popular online game |
| 184.84.240.54 | 72 | 1, 10, 11, 15 … | Unknown target hosted at Akamai |
| antiddos.solutions | 71 | — | AntiDDoS service offered at react.su. |
Looking at the most attacked services across all Mirai variants reveals the following:
- Booter services monetized Mirai: The wide diversity of targets shows that booter services ran at least some of the largest clusters. A booter service is a service provided by cyber criminals that offers on-demand DDoS attack capabilities to paying customers.
- There are fewer actors than clusters: Some clusters have strong overlapping targets, which tends to indicate that they were run by the same actors. For example, clusters 15, 26, and 6 were used to target specific Minecraft servers.
Mirai was not operated by a single entity, but by a collection of bad actors that ran their own variants for diverse nefarious purposes.
Mirai’s takedown the Internet: October 21
On October 21, a Mirai attack targeted the popular DNS provider DYN. This event prevented Internet users from accessing many popular websites, including AirBnB, Amazon, Github, HBO, Netflix, Paypal, Reddit, and Twitter, by disturbing the DYN name-resolution service.
We believe this attack was not meant to “take down the Internet,” as it was painted by the press, but rather was linked to a larger set of attacks against gaming platforms.
We reached this conclusion by looking at the other targets of the DYN variant (cluster 6). They are all gaming related. Additionally this is also consistent with the OVH attack as it was also targeted because it hosted specific game servers as discussed earlier. As sad as it seems, all the prominent sites affected by the DYN attack were apparently just the spectacular collateral damage of a war between gamers.
A gamer feud was behind the massive DDoS attack against DYN and the resulting massive Internet outage.
Mirai’s shutdown of an entire country network? October 31
Lonestar Cell, one of the largest Liberian telecom operators started to be targeted by Mirai on October 31. Over the next few months, it suffered 616 assaults, the most of any Mirai victim.
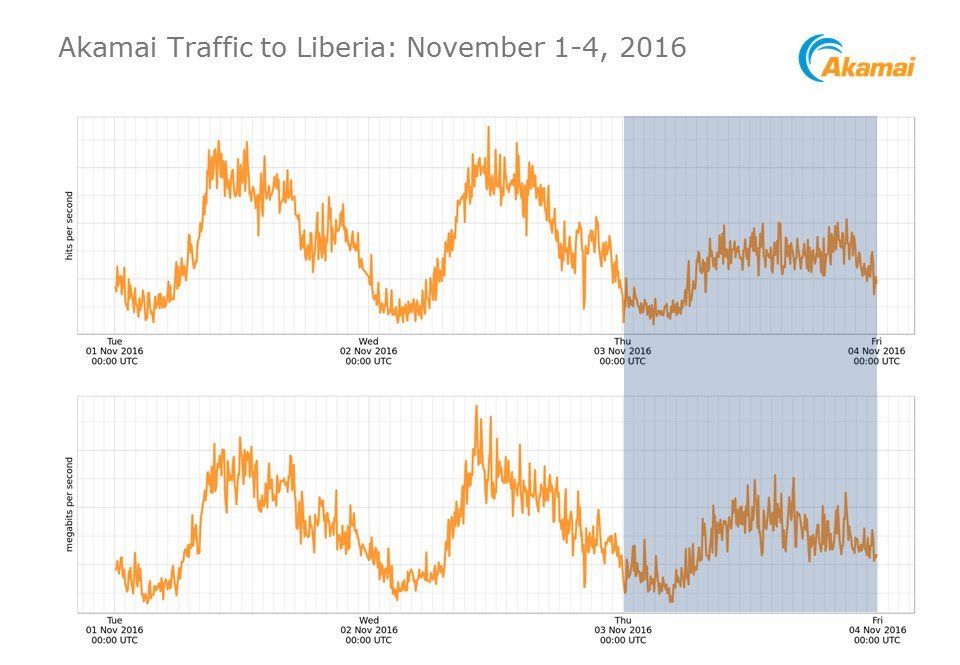
Early one these attacks received much attention due to early claims that they substantially deteriorated Liberia’s Internet general availability. For example Akamai released the chart above showing a drop in traffic coming for Liberia. However this drop was later on found to match a holiday in Liberia and the attack most likely only affected few networks.
The fact that the Mirai cluster responsible for these attack has no common infrastructure with the original Mirai or the DYN variant indicate that they were orchestrated by a totally different actor than the original author.
A few weeks after our study was published, this assessment was confirmed when the author of one of the most aggressive Mirai variant confessed during his trial that he was paid to takedown Lonestar. He acknowledged that an unnamed Liberia’s ISP paid him $10,000 to take out its competitors. This validate that our clustering approach is able to accurately track and attribute Mirai’s attacks.
The DDoS attacks against Lonestar a popular Internet provider demonstrates that IoT botnets are now weaponized to take-out competition.
Deutsche Telekom going dark: November 26
On November 26, 2016, one of the largest German Internet provider Deutsche Telekom suffered a massive outage after 900,000 of its routers were compromised.
Ironically this outage was not due to yet another Mirai DDoS attack but instead due to a particularly innovative and buggy version of Mirai that knocked these devices offline while attempting to compromise them. This variant also affected thousands of TalkTalk routers.
What allowed this variant to infect so many routers was the addition to its replication module of a router exploit targeting at the CPE WAN Management Protocol (CWMP). The CWMP protocol is an HTTP-based protocol used by many Internet providers to auto-configure and remotely manage home routers, modems, and other customer-on-premises (CPE) equipment.
Beside its scale, this incident is significant because it demonstrates how the weaponization of more complex IoT vulnerabilities by hackers can lead to very potent botnets. We hope the Deutsche Telekom event acts as a wake-up call and push toward making IoT auto-update mandatory. This is much needed to curb the significant risk posed by vulnerable IoT device given the poor track record of Internet users manually patching their IoT devices.
IoT device auto-updates should be mandatory to curb bad actors’ ability to create massive IoT botnets on the back of un-patched IoT devices.
Mirai original author outed?
In the months following his website being taken offline, Brian Krebs devoted hundreds of hours to investigating Anna-Senpai, the infamous Mirai author. In early January 2017, Brian announced that he believes Anna-senpai to be Paras Jha, a Rutgers student who apparently has been involved in previous game-hacking related schemes. After being outed, Paras Jha was questioned by the FBI. However, as of November 2017, there is still no indictment or confirmation that Paras is Mirai’s real author.
Deutsche Telekom attacker arrested
In November 2016, Daniel Kaye (aka BestBuy) the author of the MIRAI botnet variant that brought down Deutsche Telekom was arrested at the Luton airport. Prior to Mirai the a 29 years british citizen was infamous for selling his hacking services on various dark-web markets.
In July 2017 a few months after being extradited to Germany Daniel Kaye pleaded guilty and was sentenced to a one year and a half emprisonnement with suspension. During the trial Daniel admitted that he never intended for the routers to cease functioning. He only wanted to silently control them so he can use them for DDoS botnet to increase his botnet firepower. As discussed earlier he also confessed being paid by competitors to takedown Lonestar.
In Aug 2017 Daniel was extradited back to UK to face extortion charges after attempting to blackmail Lloyds and Barclays banks. According to press report he asked the Lloyds to pay about £75,000 in bitcoins for the attack to be called off.
Takeways
The prevalence of insecure IoT devices on the Internet makes it very likely that, for the foreseeable future, they will be the main source of DDOS attacks.
The Mirai incidents will go down in history as the turning point at which IoT devices became the new norm for carrying out DDoS attacks.
Mirai and subsequent IoT botnets can be averted if IoT vendors start to follow basic security best practices. In particular, the following should be required of all IoT device makers:
- Eliminate default credentials: This will prevent hackers from constructing a credential master list that allows them to compromise a myriad of devices as MIRAI did.
- Make auto-patching mandatory: IoT devices are meant to be “set and forget,” which makes manual patching unlikely. Having them auto-patch is the only reasonable option to ensure that no widespread vulnerability like the Deutsche Telekom one can be exploited to take down a large chunk of the Internet.
- Implement rate limiting: Enforcing login rate limiting to prevent brute-force attack is a good way to mitigate the tendency of people to use weak passwords. Another alternative would be using a captcha or a proof or work.
Thank you for reading this post till the end! If you enjoyed it, don’t forget to share it on your favorite social network so that your friends and colleagues can enjoy it too and learn about Mirai, the infamous IoT botnet.
To get notified when my next post is online, follow me on Twitter, Facebook, Google+, or LinkedIn. You can also get the full posts directly in your inbox by subscribing to the mailing list or via RSS.
A bientôt!




